Studying Cryptography is not new. The term Cryptography simply stands for – Hidden Writing. If you break the word ‘Cryptography’, the prefix “crypt” stands for “hidden” and the suffix “graphy” stands for “writing”.
In the current era, Cryptography stands for a technique to protect data, making the data encrypted so that ‘data breaching’ can be prevented. With a proper flowchart creator , you can create a Cryptography Flowchart easily.
There are three types of Cryptography Flowcharts, for instance – Symmetric Key Cryptography, Asymmetric Key Cryptography, and Hash Functions. You can try any of these three Cryptography Flowcharts to encrypt your data depending on your requirements.
But, why choose Cryptography Flowcharts? If your aim is to maintain data integrity, authentication, and maintain data confidentiality, then nothing could be better than Cryptography Flowcharts. Let’s go through this article and explore more Cryptography secrets.
Types Of Cryptography Flowcharts
There are three major categories that we can find in Cryptography. Following is the briefs about all three Cryptography categories or types that you should take into account:
1. Symmetric Key Cryptography
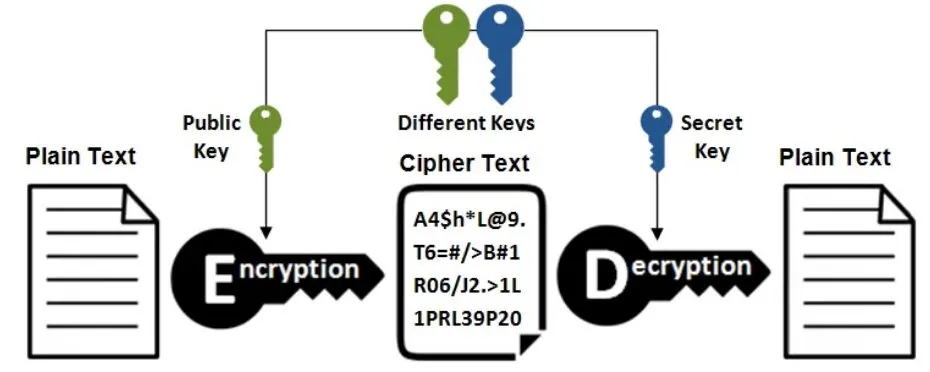
Symmetric Key Cryptography relies only on one ‘key’. Both the sender and receiver of the encrypted data can use only one ‘key’ to encrypt and decrypt the data. As you can see, only one key can do both encrypting and decrypting the data, the users have to ‘pass’ the ‘key’ securely or the confidentiality will be lost. This is a major flaw in the Symmetric Key Cryptography system.
Example: Blowfish
2. Asymmetric Key Cryptography
Asymmetric key cryptography, also popularly known as public-key cryptography consists of two keys instead of ‘one’! The involvement of two keys actually strengthens the security of Asymmetric key cryptography [better than Symmetric key cryptography]. When the ‘public key’ is distributed among the network, the ‘private key’ is not shared at all! Each user can have a unique ‘private key’ hidden. Either the public or private key can be used to encrypt the data and the remaining one can be used to decrypt the data.
Example: RSA algorithm
3. Hash Function
A Hash function is completely different from both Asymmetric and Symmetric Key Cryptography. A hash value comes with a fixed length that is calculated as per the plain text. It is hard to track the plain text, making it impossible to decipher the Hash Function. In short, the Hash Function is the toughest Cryptography that is almost impossible to crack.
Example: Passwords are encrypted using the Hash Function for OS.
Applications Of Cryptography
The application of Cryptography is more versatile than you can think of! Here are some examples of prominent uses of this technology:
1. Computer Passwords:
Creating computer passwords is the primary application of Cryptography. When it comes to creating and maintaining passwords, what could be better than using Cryptography? When a user creates a password, it is hashed. Passwords are hashed and encrypted, making it impossible to track the text and break the password.
2. Digital Currencies:
The transactions of the Digital currencies are all encrypted using Cryptography. Cryptographic keys and complicated algorithms make digital currencies safe making it hard to forge the transaction.
3. Electronic Signatures:
Another popular implementation of cryptographic keys is creating an Electronic signature. Electronic signatures today are as important as handwritten signatures. Cryptography is used to generate an electronic signature so that hackers cannot forge it easily. The public key cryptography can be used to validate electronic signatures.
4. Secure Web Browsing:
Have you ever thought about how your online browsings are protected? The prevalent use of Cryptography is to protect web browsing so that users can feel safe to share their information on the browser. Public key cryptography can be found as a Secure Sockets Layer (SSL). Transport Layer Security (TLS) protocols are implemented to encrypt data that is shared by the users.
5. Cryptocurrencies:
Not to mention, the security of the Cryptocurrency transactions also relies on Cryptography. Popular cryptocurrencies like Bitcoin and Ethereum hugely use Cryptography to safeguard data. Complex algorithms and cryptographic keys are the two pillars that ensure cryptocurrency transactions.
6. Authentication:
From accessing a bank account to logging into a secure network, the authentication process is hugely dependent on Cryptography.
7. End-To-End Encryption:
If you are using WhatsApp or similar applications, you can find the disclaimer “your data is end-to-end encrypted”. This end-to-end encryption means that two-way communications on chat or video calls are all secured. It ensures that your data is encrypted and only the receiver of the message can access the data. It provides a high level of security and maintains data privacy.
Advantages Of Using Cryptography
1. Using Cryptography ensures that only involved parties can access the data.
2. When it comes to online communication, Cryptography is the best way to protect data.
3. Implementing Cryptography in Cryptocurrency helped to eliminate various types of assaults and data breaches.
4. Cryptography can help organizations to meet legal requirements, including data protection and privacy acts.
Conclusion
Deciphering Cryptography is almost impossible and that is why it has such a strong influence in securing data online. Whether it is creating a simple password or encrypting digital transactions, Cryptography is proven to be the best. If you are concerned with data breaching and transaction security, let’s study Cryptography or find experts who can help you with implementing Cryptography and ensure security to your system.