Cybersecurity refers to the safeguarding of internet-connected systems, including hardware, software, and data, from cyber threats. Individuals and businesses use the method to prevent illegal access to data centres and other digital systems.
A robust cybersecurity strategy can give a good security posture against hostile attacks aimed at gaining access to, altering, deleting, destroying, or extorting critical data from an organization’s or user’s systems.
The necessity of cybersecurity continues to expand as the number of people, devices, and programmes in the modern company grows, along with the rising deluge of data, most of which is sensitive or confidential. The problem is compounded by the increasing number and erudition of cyber attackers and attack strategies.
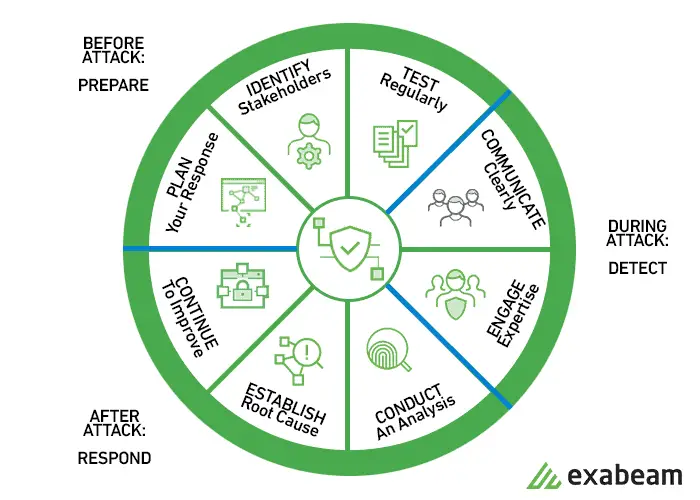
The Part of Response Phase Activities in Cyber Security
In cybersecurity, the incident response is a part of the response phase. A Cyber Incident Response Plan is a simple document that instructs IT and cybersecurity experts on what to do in the event of a security incident such as a data breach or a data leak.
It’s a process, not a single occurrence. Preparation, identification, confinement, eradication, recovery, and lessons gained are the six major steps. The majority of companies concentrate solely on containment, eradication, and recovery, ignoring any lessons acquired.
The Phases in the Incident Response Plan
A comprehensive cyber incident response strategy is required for any organization that is serious about cybersecurity. Based on research, experience, and training, this plan should be revised on a regular basis.
The strategy should be concise, clear, and precise. As a result, the stakeholders will be able to make timely judgments and implement the steps that have been outlined. It should be devoid of technical jargon. Finally, it should be personalized to your company’s unique computer systems and networks.
Source: Ascend Technologies
A phased incident response plan should be established to address a suspected data breach. There are certain areas of need that should be evaluated within each phase. Let’s take a closer look at each phase and identify the issues that need to be addressed-
1. Preparation
This phase will be the pillar of your incident response planning and, in the conclusion, the most important for protection of your company. This phase comprises the following items:
· In the case of a data breach, make sure your personnel are appropriately trained in their incident response roles and duties. Advanced Cybersecurity Training can help you out here.
· To evaluate your incident response plan, create incident response drill scenarios and conduct simulated data breaches on a regular basis.
· Ensure that all components of your incident response plan have been approved and are properly financed ahead of time.
Your response plan should be well-documented, with roles and duties for everyone clearly defined. The plan must then be put to the test to ensure that your personnel will perform as expected. The better your personnel are prepared, the less likely they are to make significant errors.
2. Identification
This is the procedure for determining whether or not you’ve been hacked. A breach, also known as an incident, can occur in many ways. During this point, it’s also crucial to keep track of everything.
3. Containment
When a security compromise is first discovered, your first reaction may be to securely remove everything so you can go on. However, this will likely backfire in the long run because you’ll be losing crucial evidence needed to figure out where the breach began and design a plan to prevent it from happening again.
Instead, confine the breach to prevent it from spreading and causing more harm to your company. Disconnect impacted devices from the Internet if possible. Prepare both short- and long-term containment plans.
It’s also beneficial to have a redundant system backup in case business operations are disrupted. In that manner, any data that has been compromised will not be gone permanently.
Update and patch your systems, evaluate your remote access protocols, change all user and administrative access credentials, and strengthen all passwords now.
4. Eradication
After you’ve contained the problem, you’ll need to locate and eliminate the breach’s fundamental cause. This means that all malware should be removed safely, systems should be hardened and patched anew, and updates should be installed.
Whether you do it yourself or hire someone to do it for you, you must be thorough. If any traces of malware or security flaws remain in your systems, you risk losing important data and increasing your liabilities.
5. Recovery
This is the procedure for repairing and reinstalling damaged systems and devices in your company’s environment. It’s critical to get your systems and business activities back up and running without risk of another breach during this time.
6. Lessons Learned
Conduct an after-process meeting with all members of the Incident Response Team to share what you’ve learned from the data breach. This is where you will investigate and document the security violation. Determine what aspects of your reaction plan worked successfully and where there were flaws. Lessons gathered from both simulated and real-world occurrences will aid in the strengthening of your systems against forthcoming attacks.
Although no one wants to experience a data breach, it is necessary to prepare for one. Prepare for it, know what to do if it occurs, and study everything you can about it afterwards.
FAQs
1. What is the definition of a cyber security response plan?
A cybersecurity incident response plan is a set of guidelines designed to assist businesses in anticipating, detecting, responding to, and recovering from network security problems.
2. What are the differences between the two sorts of incidents?
One strategy is to limit events to two types: accidents and near misses.
3. How long does it take for a security breach to be discovered?
A breach’s cost extends beyond the amount of data lost or revealed, depending on how long it takes to recover it.